Towards total security: Bridging SOC 2 with ISO 27001
Beatrice van der Velden
Legal Assistant at NAALA
Published on 25 April, 2024
By: Beatrice van der Velden – Legal Assistant at NAALA
Published on 25 April, 2024
High-profile data breaches have become a serious threat to companies in the complex landscape of cybersecurity and data privacy. How can you best protect against these threats? International standards like ISO 27001 and SOC 2 can give you guidance. But which standard is more suitable for your organization, and how can you implement these effectively without consuming too much of your team’s valuable time? Let’s have a look at the similarities and differences between these standards.
What is SOC 2?
- SOC 2 is a cybersecurity compliance framework specifying how organizations should protect customer data from unauthorized access, security incidents, and other vulnerabilities.
- It was developed by the American Institute of Certified Public Accountants (AICPA) based on five principles (Trust Services Criteria): security, availability, processing integrity, confidentiality, and privacy.
- SOC 2 compliance involves an independent audit conducted by certified professionals to assess an organization’s adherence to the framework’s principles.
What is ISO 27001?
- ISO 27001 is a globally recognised standard providing a framework for establishing, implementing, maintaining, and continually improving an information security management system (ISMS).
- Unlike SOC 2, which focuses on service providers, ISO 27001 is applicable to any organization, regardless of size, industry, or sector. It ensures availability, confidentiality and integrity of information.
- To be ISO 27001 certified, a third-party auditor must verify that you meet the compliance requirements.
Key Differences between ISO 27001 and SOC 2
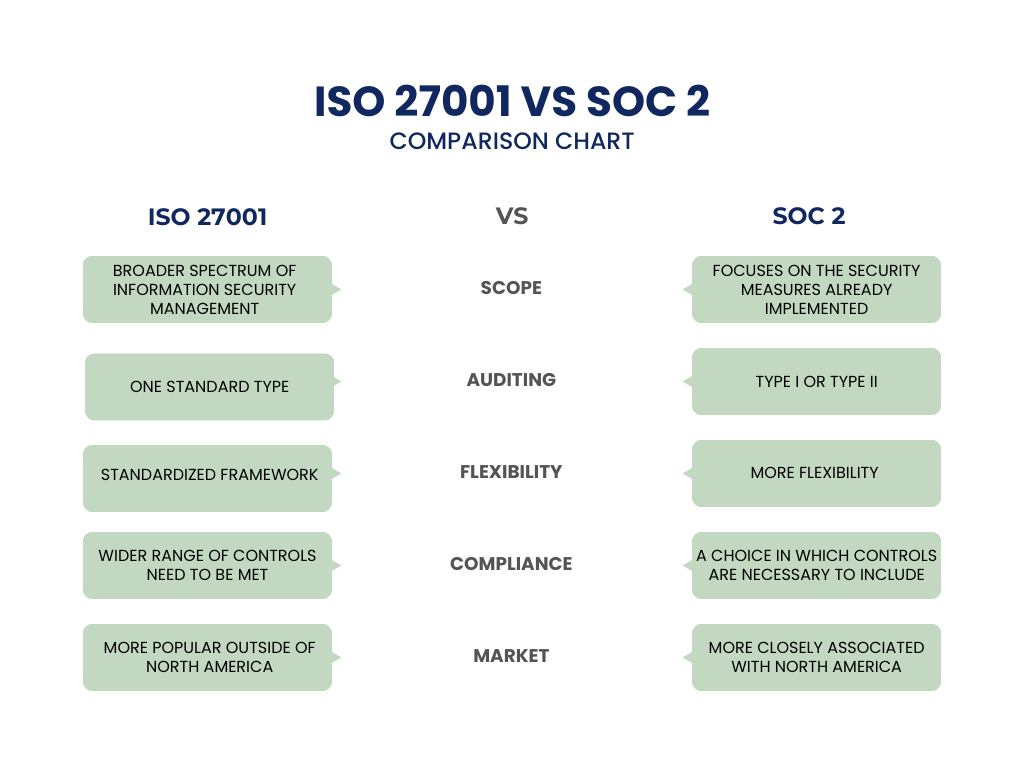
- Scope: SOC 2 primarily addresses service providers’ handling of customer data, focusing on the security measures already implemented in the organization. ISO 27001 however applies to the broader spectrum of information security management within an organization. In addition, it requires an ISMS to maintain availability, confidentiality and integrity of information.
- Auditing Process: SOC 2 requires a specific type of audit conducted by certified public accountants (CPAs). There are two types of SOC 2 audits, type I and type II. Type I evaluates an organization’s security program at a single point in time, whereas type II evaluates a longer term. SOC 2 compliance is documented with a formal attestation. ISO 27001 only has one audit process, after which a certificate of compliance is granted.
- Flexibility: SOC 2 offers more flexibility in terms of implementation, allowing organizations to tailor security measures to their specific needs, whereas ISO 27001 compliance follows a standardized framework.
- Compliance requirements: For SOC 2 reports, only the security category of the Trust Service Criteria is required. As for the other controls, they can be included in the SOC 2 report at the organization’s discretion.
- Market applicability: Both frameworks are recognised globally, but SOC 2 is more closely associated with North America. If you’re based in that region, you’ll find that both SOC 2 and ISO 27001 are common. Outside of North America, ISO 27001 is much more popular.
Key Similarities between ISO 27001 and SOC 2
Despite some differences, SOC 2 and ISO 27001 also share various common principles:
- Both are internationally recognized standards and are accepted worldwide.
- Both standards act as a guidance for implementing best practices in information security, safeguarding both your organizational data and the sensitive information of your customers.
- The frameworks share mostly the same security controls for policies, processes, and technologies designed to protect sensitive information.
- Both frameworks are made up of three distinct stages.
In choosing between SOC 2 and ISO 27001, a company should consider whether an ISMS is in place, the customer’s industry and the type of customers. Most companies however comply with both standards, as they are not interchangeable due to its own purpose and market it serves.
Implementing SOC 2 and ISO 27001 with NAALA
While each standard has its unique focus and requirements, implementing them effectively is essential for mitigating risks and demonstrating commitment to security best practices.
NAALA’s comprehensive toolkits provide organizations with the necessary resources to streamline the implementation of SOC 2 and ISO 27001 standards.
Ready to embark on your compliance journey? Explore NAALA’s solutions today and request our toolkits here.
Questions? We are happy to discuss your specific case.
Related
Although the word “trend” typically sparks your curiosity, when paired with “information and cyber security”, we encourage you to be vigilant and mindful of the challenges foreseen. The landscape of information and cyber security is ever-changing, and 2024 brings its own set of challenges.
Interested in staying ahead in the ever-evolving landscape of information security? Explore our blog for an in-depth look into the recent revisions of ISO 27001:2022. Discover the key changes, implementation challenges, and the benefits of upgrading to the latest standard.
Please note that all details and listings do not claim to be complete, are without guarantee and are for information purposes only. Changes in legal or regulatory requirements may occur at short notice, which we cannot reflect on a daily basis.